In the data sharing digital landscape that Travis County has, it is imperative when sharing data that qualifies as PHI, we are all using the de-identification methods that are in accordance with the HIPAA Privacy Rule, so unauthorized uses and disclosures are limited, as we all have a role in safeguarding this data.
Protected Health Information (PHI)
PHI is information, including demographic information, which relates to an individual’s past, present, or future health condition, treatment for the condition, or payment for the treatment. PHI includes many common identifiers (e.g., name, address, email address, SSN, DOB, driver’s license number, etc. ) when they are associated with the health information.
- Identifying information alone, such as first and last name, residential address, or phone number, would not be designated as PHI.
- If such information was available through a publicly accessible data source, such as a phone book, then this information would not be PHI because it is not related to heath data.
- Identifying information together, such as first and last name, residential address, phone number, an individual’s health condition (asthma), the treatment service for the asthma, and the current payment amount for the medical visit, this would be designated as PHI.
- In order for this PHI information to become available to share, the individual would need to provide consent, as it does relate to the individual’s health data.

What is De-identification?
De-identification is a process that ensures the individually identifiable PHI cannot be used to identify a specific individual and it also protects the privacy of the individuals when addressed by people who should not know the person’s identity. This is achieved by removing certain data elements from a designated data set.
Designated data set in the context of PHI refers to a group of records maintained by or for a covered entity. Data sets could be medical billing, benefits, case files, invoices for treatment of services, reports that need to be sent to the state for grants, etc.
Why Is De-identification Important?
- Compliance with Regulations: The HIPAA Privacy Rule mandates the de-identification of PHI before it can be disclosed.
- Limits Privacy Risk Exposure: It protects individuals PHI data and there is a decrease in incidents/breaches.
- Data Sharing: When PHI is de-identified, the identity of individuals is protected and cannot be determined, and re-identification of individuals is not possible, then PHI can be shared.
- Trust and Reputation: It helps build trust with customers, clients, and stakeholders. If an organization fails to protect PHI data, it can damage its reputation and lose the trust of its customers.
- Prevents Identity Theft: It helps prevent identity theft. If PHI data is stolen, it can be used to commit fraud or other criminal activities.
- Reuse: It makes it easier for covered entities to share the data set when doing business with third-party vendors.
HIPAA Privacy Rule De-Identification Methods
Section 45 CFR § 164.514(b) of the HIPAA Privacy Rule provides two methods by which PHI can be de-identified. When sharing PHI data, the following methods must be followed in order to meet the de-identification standard. They are the Safe Harbor method and Expert Determination method.
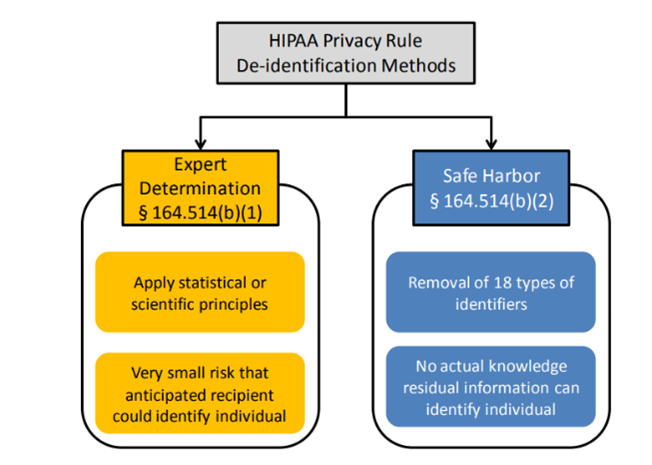
Neither method will remove all risk of re-identification of individuals, but both methods will reduce risk to a very low and acceptable level.
The Safe Harbor method (the most common approach) provides a way to de-identify PHI to ensure the privacy of individuals. Under this method a covered entity determines one or more of the below identifiers need to be removed from the designated data set so the specific individual cannot be identified.
Identifiers
| Names (including Nicknames) | Geographic subdivisions smaller than a state (including street address, city, county, precinct, zip code) |
| Dates (except year), including birthdate, admission date, discharge date, and date of death | Telephone and Cellphone Numbers |
| Email Addresses | Social Security Numbers |
| Medical Record Numbers | Health Plan Beneficiary Numbers or Member ID Numbers |
| Account Numbers | Certificate/License Numbers |
| Credit Card and Bank Account Numbers | Vehicle Identifiers and Serial Numbers including License Plates |
| Device Identifiers and Serial Numbers | Website URLs |
| Internet Protocol (IP) Addresses | Full Face Photos and Comparable Images |
| Biometric Identifiers (including finger and voice prints) | Tattoos/Scars |
| Doctor Names | Dates associated with test measures, such as those derived from a laboratory report |
| Clinical Trial Numbers |
The Expert Determination method requires a formal determination that is documented by an expert based on their knowledge and experience (statistical, scientific principles) with de-identifying PHI data.
Some Principles To Include Are:
- Replicability - Prioritize health information features (results of blood glucose levels) into levels of risk (L/H) according to the chance it will consistently occur in relation to the individual.
- Distinguishability - Determine the extent to which the subject’s data can be distinguished in the health information. This is a % result of the identifiers that could be identified in the U.S. that year.
- Assessment of Risk - The greater the replicability (lab values are rarely independently replicable and not many people have access) and distinguishability (demographics are highly replicable and available in public sources) of the health information, the greater the risk (L/H) for identification.
Scenario Examples: When De-identification Needs To Occur
In the below scenarios the identifying information is associated with PHI and could be tied back to an specific individual:
- A medical record, laboratory report, or hospital bill that contains an individual’s name, DOB, address, SSN, medical condition, and treatment plan.
- An invoice that has been paid needs to be submitted for an insurance claim. The invoice has the individual’s name, address, phone number, clinic’s name and address, physician’s name, SSN, details of the health services, and x-ray results.
- A case file that has a notes free text field detailing the individual's history of kidney stones and a list of medications. The file also contains the name, address, and age of the individual.
Risk Reduction Methods To De-Identify Data
Data Redaction is a data masking method. It involves removing or substituting all or part of the field. It is often used when sharing data and making it publicly accessible.

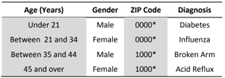
The Suppression method is where certain data values are removed or replaced entirely if a substantial quantity of records is considered too risky (removal of age and zip code) to share.

The Generalized method will transform data into a more abstract representation. A five-digit zip code may be generalized with numbers and a special character, and an age of an individual may be generalized from one - to thirteen-year-old age groups.
In closing, there is no preferred method to use when de-identifying a designated data set, the important point is to ensure it cannot be tied back to a specific individual, and the individual’s PHI is protected.
If you would like general information about HIPAA, click to view the HIPAA page. Here you can find all the HIPAA policies or to report a suspected privacy concern.
