Summer is right around the corner, and it will be time for some sun, fun, exploration and relaxation. Unfortunately, as you unwind, there are cyber criminals who gear up to take advantage of our moments of diversion and distraction. Scammers love summer, too, as your data is a goldmine to them!

Before you head out on that road trip, to the coast, or that vacation abroad out of the country, below are some reminders around protecting your data and some common scams that can turn a much-needed break from work into a break-the-bank moment.
Proper Ways for Protecting County Issued Devices
Leave County Issued Devices (Laptops, Mobile Devices, iPAD, Cameras etc.) In The Hotel Safe
Use the safe to store any County issued devices you won’t need for the day, like a laptop, mobile devices, USB drive, external hard drive, or wearable technology.
- NEVER leave county issued devices out in plain view in the hotel room.
- NEVER leave county issued devices unattended in the vehicle where others can see them.
- This includes under the front or back seats.
- County issued devices should only be stored in a completely secure trunk.
- Note, a trunk is a covered storage area. If you have a hatchback or window that can be broken into above the trunk area, this is not considered secure
- We recommend taking the device(s) with you or storing them in another locked area.

Protecting Your Personal Data
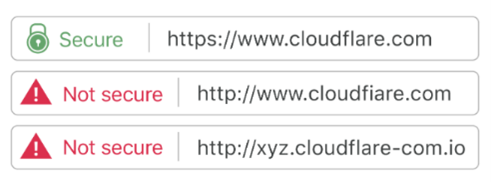
Book Travel From Secure Websites
When booking anything travel-related, be sure to go directly to the official website of the company to book your reservations. The site’s web address should have “HTTPS” in the URL.
Turn off Automatic Bluetooth Connectivity
Bluetooth is great in the car or at home, where it’s safe to communicate with other electronic devices. But most of us forget to disable Bluetooth connectivity when we go to public places, especially when we go on vacation. With your Bluetooth connectivity left open, anyone sitting in a hotel lobby or nearby coffee shop could pick up that signal and gain access to your device. This can happen quickly and without your knowledge.
- How to Enable or Disable Bluetooth on iPhone and iPad (howtogeek.com)
- How to Enable or Disable Bluetooth on Android (howtogeek.com)
Only use Password-Protected Wi-Fi Networks – Avoid “Free”
Other countries may not have the same regulations on public Wi-Fi as the U.S. does, so sticking to a password-protected network, like the ones offered at most major hotels, is likely your safest bet if you need to access the Internet. Always use a secure, private network especially when accessing personal or financial accounts and always ensure you’ve logged out of your account before leaving and avoid connecting to public Wi-Fi.
Use a VPN
VPN, an acronym for virtual private network, allows you to access the public internet via a secure and private network connection. Think of a VPN as a secret tunnel that bypasses a busy highway: it allows you to skip all the bad drivers and speed traps and arrive at your destination unscathed. A virtual private network hides information about your physical location while securing your digital data through encryption. VPNs are an incredible tool for maintaining privacy while traveling or using public WiFi, or even while using the Internet at home.
Passwords
Never write your passwords down, never share them, and never use the same passwords for multiple accounts. Instead, use a password manager to store them.
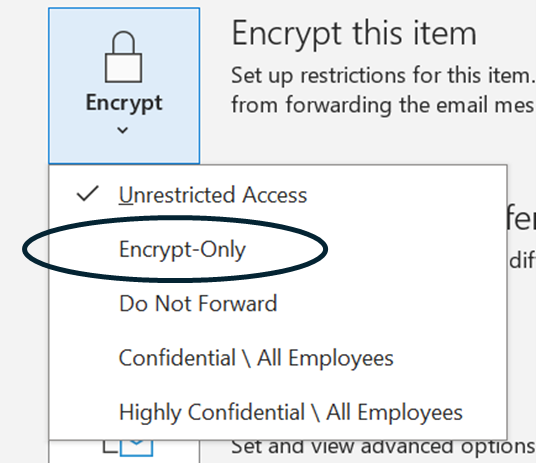
Use Email Encryption
Email encryption is a security measure that encodes an email message so that only the intended recipients can read it. It ensures that the content remains confidential and protected from unauthorized access by entities other than the designated recipients. If you need to send email, always ensure it is encrypted, and send it over a secure Wi-Fi network.
- How to send an encrypted email is here.
- Alternatively, you can encrypt an email by Opening Outlook, Open a New Email, Click on File, Click on Encrypt this item.
Check Sensitive Accounts Regularly
Before you leave for a day of activities, get in the habit of checking sensitive financial accounts. The sooner you spot unfamiliar or fraudulent behavior, the better. Just make sure you log out of your accounts after each use.
Don’t Broadcast your Vacation on Social Media
As tempting as it may be to share your vacation experiences online, it’s unwise to broadcast your location every few hours on social media. Why? You could be revealing that you’re not at home, where you may have left important personal data unsecured. And let’s not forget about all the other valuables you have inside your house. Post your vacation pictures after you get back home and limit info on your specific whereabouts when using social media.
SCAM Reminders
Discounted/Prize Vacation Packages Scams
Fake discounted/prize vacation packages are running rampant online, particularly on social media. On platforms like Instagram and Facebook, you might have seen targeted ads for steeply discounted vacation packages to exotic destinations like Bali or the Maldives. If it seems too good to be true, it's probably a scam — unfortunately, there's just no way you can get a week-long stay at a luxury overwater bungalow in the Maldives for $500!

Hotel Scam - Fake Front Desk Calls
Scammers will call hotel rooms impersonating the front desk person. “The caller claims there’s a problem with the card on file and asks the traveler to “re-verify” the credit card information.” The scammer will offer to take your credit card information over the phone so that you’re not inconvenienced. However, a real hotel staff member will never ask for your credit card information over the phone. They will always ask to settle any charges at the front desk.

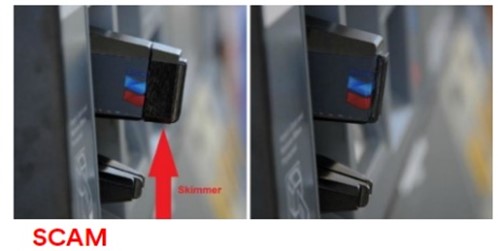
Credit Card Skimming Scams
No matter where you go, a scammer could use a card skimmer to steal your credit card information. A skimmer can be attached to an ATM or gas pump. When you are using your card at an ATM or at the pump, pay attention to the card reader. Does it stick out farther than normal or is the card reader loose? The best thing you can do is monitor your accounts for suspicious activity and make sure you keep your wallet in a secure place.
Artificial Intelligence (AI) Scams
Voice Cloning Scams
Voice Cloning scams are growing. They are a type of fraud that involve the use of artificial intelligence (AI) to clone an individual’s voice and impersonate them. To achieve this, the scammer records your voice and creates a deepfake version of your voice using AI. This can be done in a matter of seconds.
Not only can AI be used to clone celebrities and public figures, but it can also be used in claiming to be friends of yours, family, or co-workers. The technology is so advanced that scammers can add accents, age ranges, background sounds, etc. These AI-fueled scams have many variations, ranging from gaining unauthorized access to your financial and personal information, to election misinformation, or virtual kidnapping scams for ransom.

An example of a voice cloning scam was an incident in which a cybercriminal attempted to extort $1 million from an Arizona-based woman whose daughter he claimed to have kidnapped.
Deepfake Scams
Deepfakes are manipulated images, audio, and video that are created using artificial intelligence (AI) techniques. Deepfake scams try to convince viewers that their product or platform is legitimate and worth investing in because it’s been endorsed by someone the public knows or trusts.
Video Impersonation - This is a well-known deepfake scam where there is a made-up video generally resembling a high-profile target. A typical victim can be a president of a country (Obama), a popular rock star (Taylor Swift), or a CEO of a well-known company (Jeff Bezos, Elon Musk). What makes them easy targets is the public availability of their pictures, speeches, etc., because the tools creating deepfake videos perform well with dissimilar input, depicting different ranges of emotions, facial angles, lighting conditions, backgrounds, and more. The intention of such impersonation can be a blackmail attempt, political motivation, defamation, or anything else.
This is not Morgan Freeman - A Deepfake Singularity (youtube.com)

Fake News - Such online disinformation campaigns pose risks that can prove fatal in tricky situations like riots or wars. Not only this, but it can also malign public figures when their deepfake replica makes comments they never did in reality. What helps the propaganda is the social media and streaming platforms like YouTube, and Meta, which help such fake news spread like wildfire. Finally, it creates an atmosphere where normal users get confused about the authenticity of everything they see.
How To Stay Safe From AI Scams:
- Use antivirus/antimalware software.
- Let unknown calls go to voicemail.
- End a suspicious call and calling back the number to assess the person’s authenticity.
- Call friends or family directly to verify their identity, or come up with a safe wordto say over the phone to confirm a real emergency.
- Use additional authentication methods such as two factor authentication or biometric authentication (e.g., fingerprint or facial recognition), in conjunction with voice ID.
Phishing Scams
Phishing is a scam that impersonates a reputable person or organization with the goal to steal personal and financial information, such as login credentials, credit card numbers, and other sensitive data. Although email is the most common type of phishing attack, there are a few others that fall under Phishing to be aware of. They are:
- Vishing scams happen over the phone, voice email, or VoIP (Voice Over Internet Protocol) calls.
- Smishing scams happen through SMS (text) messages.
- Pharming scams happen when malicious code is installed on your computer to redirect you to fake websites.
- Spear Phishing scams are an attempt that targets a specific individual or group of individuals.
- Whale Phishing (Whaling) scams are a type of spear-phishing that targets a high-profile victim, such as a CEO or CFO. Whaling attacks usually employ a sense of urgency to pressure the victim into wiring funds or sharing credentials on a malicious website.
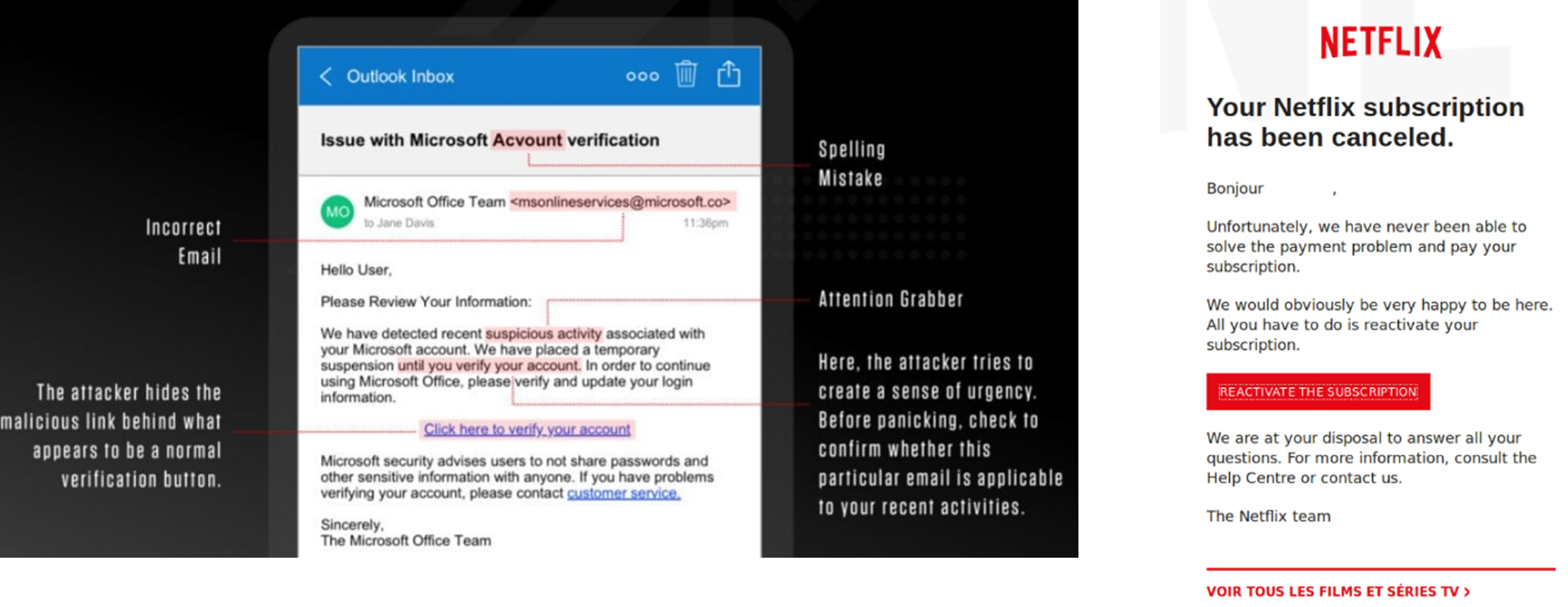
Phishing Email Scams send an email that appears to be from a trustworthy source, such as a bank or well-known company, asking the recipient to click on a link or provide sensitive information. The link in the email leads to a fake website that looks legitimate but is actually controlled by the attacker.
Some Examples of Phishing Email Scams:
- Fake Invoice scam: You receive an email with an attached invoice for a purchase you never made.
- Email Account Upgrade scam: You are asked to verify your email account or update your password by clicking on a link.
- Advance-Fee scam: You are promised a large sum of money if you pay a small fee or share your bank details.
- PayPal/Zelle scam: You are notified of a problem with your PayPal/Zelle account or a payment you never authorized.
How To Stay Safe
- Don’t click on anything in an unsolicited email or text message. Look up the company’s phone number on your own (don’t use the one a potential scammer is providing), and call the company to ask if the request is legitimate.
- Carefully examine the email address, and spelling used in any correspondence. Scammers use slight differences to trick your eye and gain your trust.
- Be careful what you download. Never open an email attachment from someone you don’t know and be wary of email attachments forwarded to you.
Banking Scams
Bank scams are a common way for criminals to gain access to people’s personal and financial information. Banks will never call you. Instead, they will send you an email if they need to get in touch with you.
Check Cooking/Check Baking Scams
Scammers have taken check washing to a new level called “check cooking” or “check baking.” It’s much more lucrative, efficient, and allows them to easily manufacture dozens of checks and deposit them into numerous drop accounts. This is when cybercriminals take a digital picture of a stolen check then use commercially available software to alter it. It looks very real, even with the watermarks and all. Criminals can print new phony checks or deposit the altered image using a bank’s mobile app and by the time it’s noticed, the scammer could have made away with thousands of dollars. Lastly, if the check amount seems to go to be true, do not cash it. Always take it to a bank to have it verified.

Overpayment Scam
Overpayment scams typically begin with someone sending you a counterfeit check or money order for more than the amount owed. Then, they ask you to deposit the money in the bank and wire the difference back to you. Unfortunately, since the check was fake, you could owe the bank a returned check fee.
Unsolicited Bank Fraud
Have you ever received a check in the mail that you weren’t expecting? It could look like a rebate check or a refund for overpayment. Inspect the check thoroughly, paying close attention to any fine print on the front or back. There’s a chance that you are entering into a legally binding contract by signing the check and cashing it. Scammers use tactics like this to get you to authorize memberships, loans and other longer-term commitments that could cost you dearly.
How to Stay Safe
- Consider always using a credit card when traveling.
- Continually monitor your personal and business checking account, watching for suspicious transactions.
- Don’t cash checks for other people. You may want to help other people, but never cash a check in exchange for cash unless you know the person well.
- Do your homework. Read and inspect everything. Whether it’s an email, text or arrives in another form, always read the fine print. If an offer looks suspicious or too good to be true, it probably is.
- Don’t share personal information.
- Use your best judgement.
If you think you may have been targeted by a SCAM, report it to:
- The FTC at ftc.gov
- Internet Crime Complaint Center(IC3) | Home Page
- Report it to BBB Scam Tracker at org/scamtracker
In closing, being aware of the scams out there and knowing how to stay safe will make it easier in protecting your personal data, and you will be able to enjoy your vacation more!
If you would like general information about HIPAA, click to view the HIPAA page. Here you can find all the HIPAA policies or to report a suspected privacy concern.
