Information Security

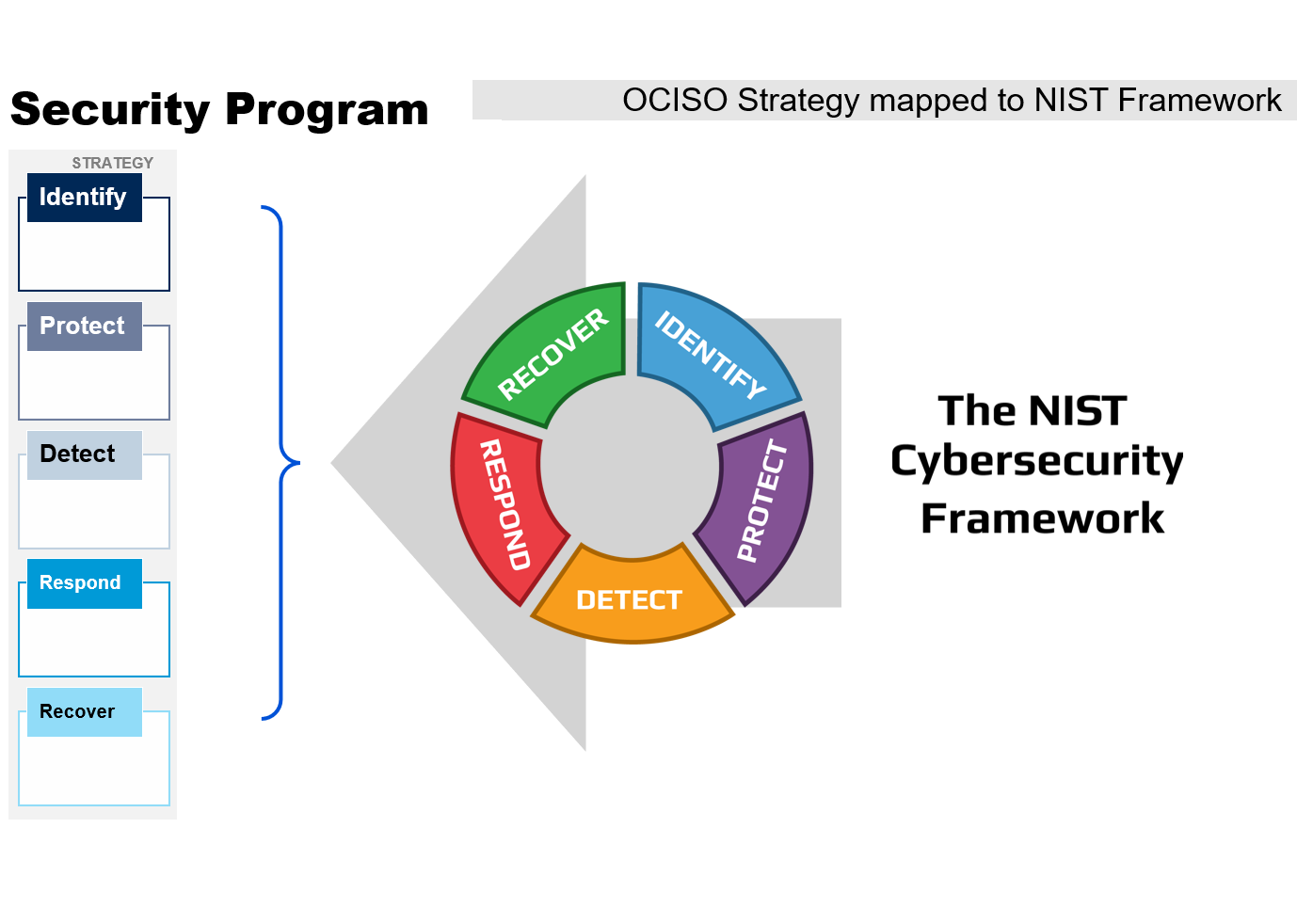
The Security Program is based on the National Institute of Standards and Technology (NIST) Framework to form 5 Pillars:
IDENTIFY
Develop an organizational understanding to manage cybersecurity risk to systems, people, assets, data, and capabilities.
DETECT
Develop and implement appropriate activities to identify the occurrence of a cybersecurity event.
PROTECT
Develop and implement appropriate safeguards to ensure delivery of critical services.
RESPOND
Develop and implement appropriate activities to take action regarding a detected cybersecurity incident.
RECOVER
Develop and implement appropriate activities to maintain plans for resilience and to restore any capabilities or services that were impaired due to a cybersecurity incident.
MISSION
The mission of the Office of the Chief Information Security Officer is to safeguard personal and institutional data through a culture of shared responsibility and accountability
VISION
We will collaboratively create a risk-aware culture that places high value on efficiently protecting information entrusted to Travis County
BUSINESS AREAS
SECURITY OPERATIONS
Security Operations primary responsibility is to select, maintain, and monitor the tools that identify and defend against threats to the organization’s information systems. That includes participating in the identification of threats, the management of vulnerabilities, and the response to security incidents.
INFORMATION ASSURANCE
Information Assurance supports Travis County justice, health, and safety services systems by defining the level of security controls to protect systems and information against unauthorized access, disclosure, modification or destruction, whether accidental or deliberate, as well as assure the confidentiality, integrity, and availability of information.
INCIDENT RESPONSE
The TRAVIS COUNTY INCIDENT RESPONSE PLAN documents the policy, procedure and response in detail.
WHAT is an incident and WHY report it?
An IT security incident includes suspected activity with:
- Compromised user accounts
- Computer system intrusion
- Ransomware infection
- Denial-of-service attack
- Unauthorized access, use, disclosure, modification, or destruction of information, data, systems, software, or changes to them
- Loss or theft of equipment used to store or work with sensitive Travis County data
- Interference with the intended use of IT resources
- Interference with information technology operation
- Violation of explicit or implied acceptable use policy
We can help resolve an incident and aid in the recovery of accounts, data assets and/or mitigate the risk impacts to them.
Travis County falls under several electronic data regulatory and standards regimes, it is Travis County policy to report IT security incidents; see TC-ITS-125, Security Incident Procedures Policy
HOW TO REPORT
Report security incidents as soon as possible to the ITS Helpdesk
If aspects of the incident pose physical danger, call 911 to contact law enforcement authorities immediately.
Phone: 512-854-9175
Email: ITS.Helpdesk@traviscountytx.gov
Web: Online request form (in-network)
SECURITY AWARENESS RESOURCES
Newsletters, safety tips, and optional video shorts are provided below to level-up cyber security knowledge and awareness.
STOP | THINK | CONNECT SAFETY TIPS:
KEEP A CLEAN MACHINE
- Automate software updates
- Add virus protection to all devices that connect to the internet
- Virus scan anything you plug in
PROTECT YOUR PERSONAL INFO
- Enable strong login, use multi-factor authentication, and create strong password sentences
- Have separate passwords for every unique account
- Use a password manager or keep your password list stored in a secure place away from PC
CONNECT WITH CARE
- Delete old email with links, social media posts and online advertising
- Limit business you conduct to hotspots you trust and use your VPN
- Use security enabled sites when banking and shopping (web addresses with “https://” or “shttp://”)
BE WEB WISE
- Stay current with cyber information from trusted sites: Stay Safe Online or CISA
- Don’t click suspicious links, check with the source yourself
- Back up your important information in 3’s (online, local site, different location)
BE A GOOD ONLINE CITIZEN
- Think about what you do online, it has the potential to affect everyone
- Golden Rule: Post only about others as you have them post about you
- Report cybercrime (stolen finances or identities ) to the Internet Crime Complaint Center (www.ic3.gov)
OWN YOUR ONLINE PRESENCE
- Personal information is like money. Value it. Protect it
- Be aware of what’s being shared and share with care
PHISHING CAMPAIGNS
Information Security regularly conducts phishing campaigns with fake/test phishing emails to both gauge and improve the security awareness of Travis County employees. Below is a sample test that was issued in 2023.
| TEST PHISHING EMAIL: | WHAT SHOULD YOU DO? | WHAT YOU WOULD SEE: |
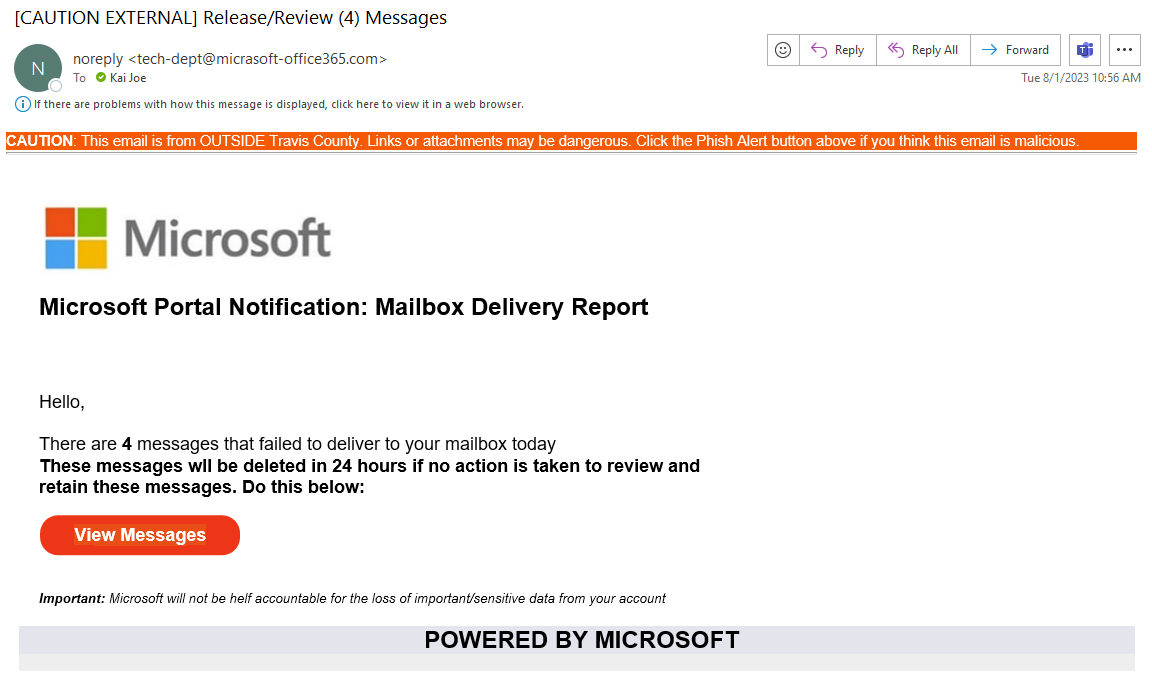 |
Report the Phish!  |
IF you clicked the link, you would see the following page: 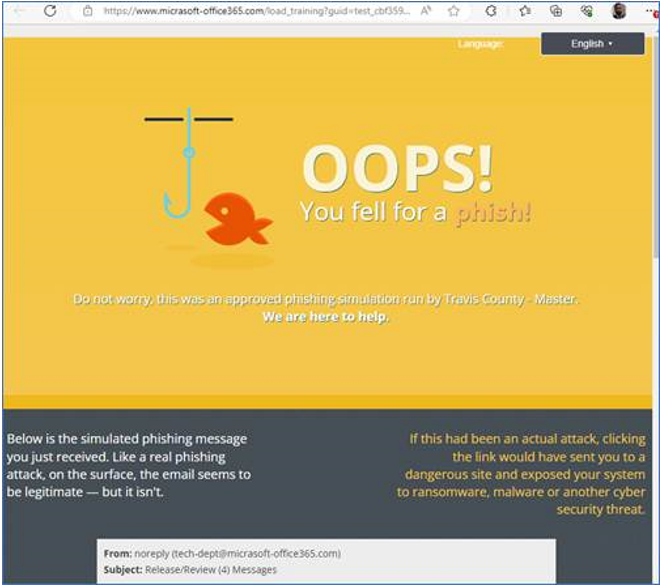 |
WHAT TO LOOK FOR: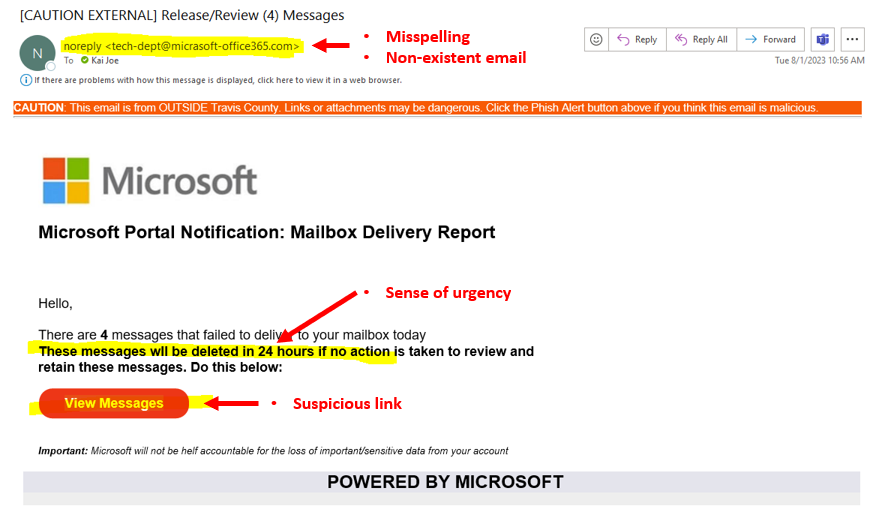 |
IF you click "Report Phish" in Outlook, you see a pop-up: 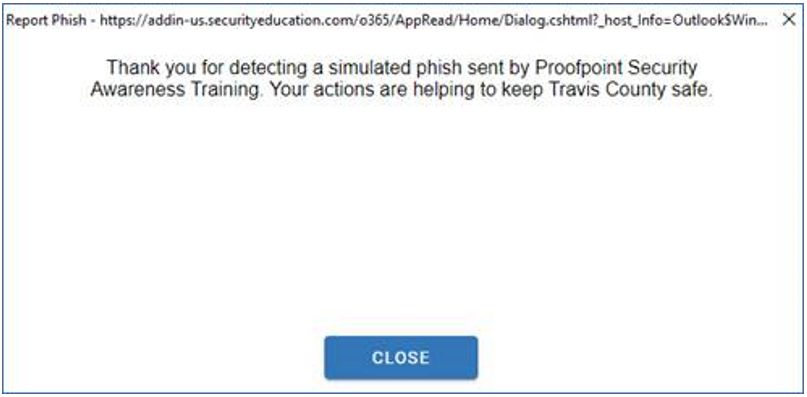 |
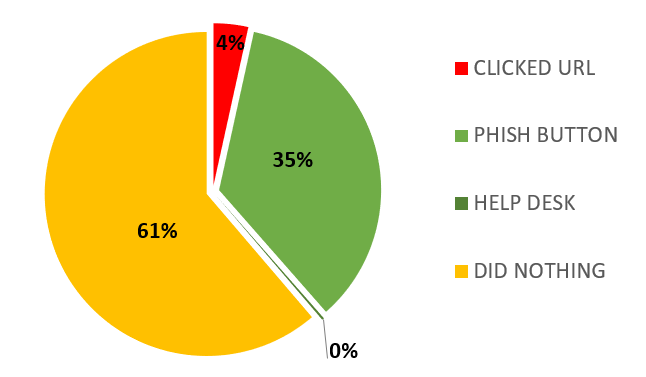
2024 Scoreboard
Below are the phishing campaign results conducted in 2024 across all departments.
| QUARTER | EMAIL RESPONSE % | OVERALL ACTIONS TO PHISH % |
| Q2 | 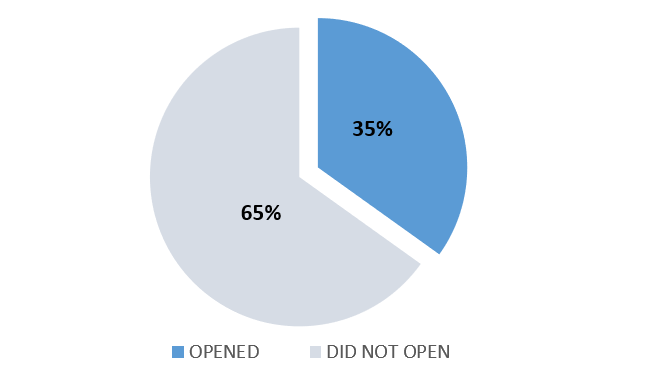 |
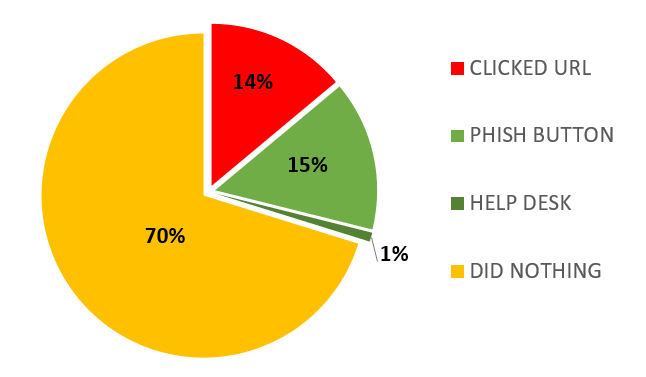 |
| Q1 | 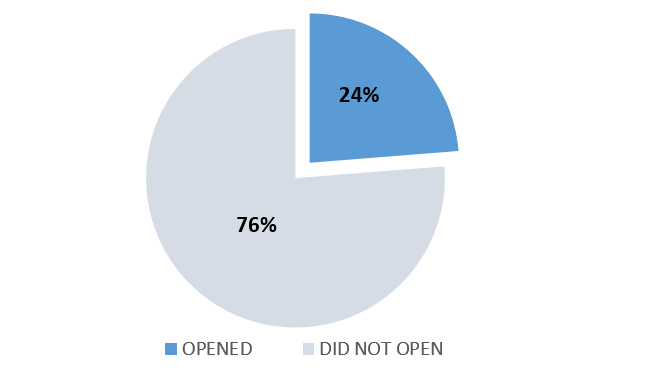 |
 |
NEWSLETTER & OPTIONAL TRAINING:
Email or Print out these posters and Newsletters to help staff stay informed of cyber security related topics.
Optional video and other related cyber training shorts are available to aid in improving staff knowledge.
! ** NOTE ** These links WILL take you externally to KnowBe4.com, just enter your work email to enter ---- !
- Phishing - TBD
- Working Remotely - TBD
- Ransomware - TBD
- Mobile Devices – TBD
- PCI DSS - TBD
CYBERSECURITY AWARENESS MONTH 2023 WINNERS
Contact kai.joe@traviscountytx.gov to schedule a meetup at the office to get your prize!
Congratulations to the following winners:
| WEEK | CHALLENGE MODULE COMPLETED | WINNER |
|---|---|---|
| 1 | Data Protection: Introduction to Data Protection | Nohelia Villeda |
| 2 | Ransomware: Beating Ransomware | Rachel Deleery |
| 3 | Social Media and AI: QR Codes, Spotting a Deepfake | Yarelyn Perez |
| 4 | You Can Make a Difference: Security Culture and You | Gaby Villatoro |
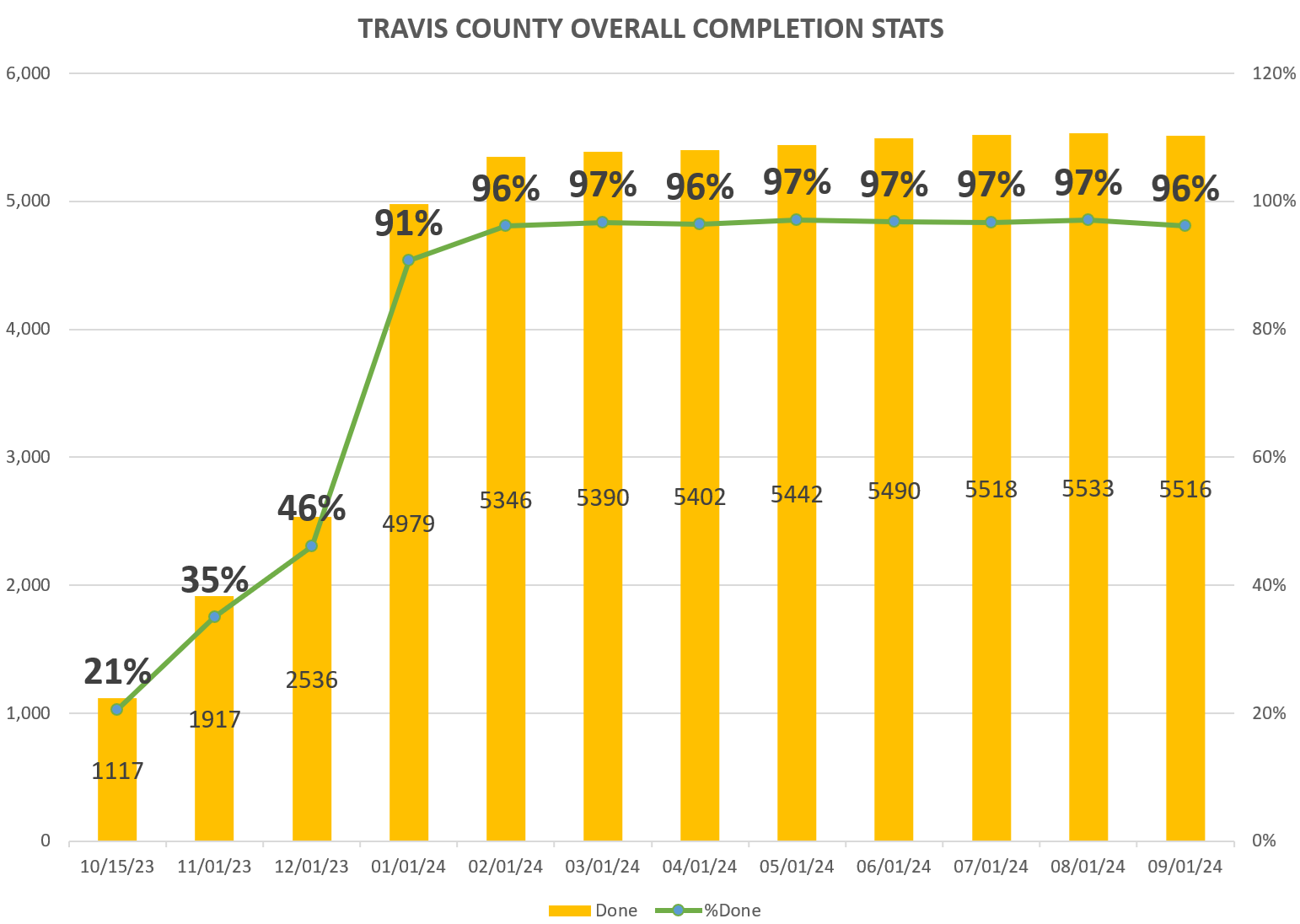
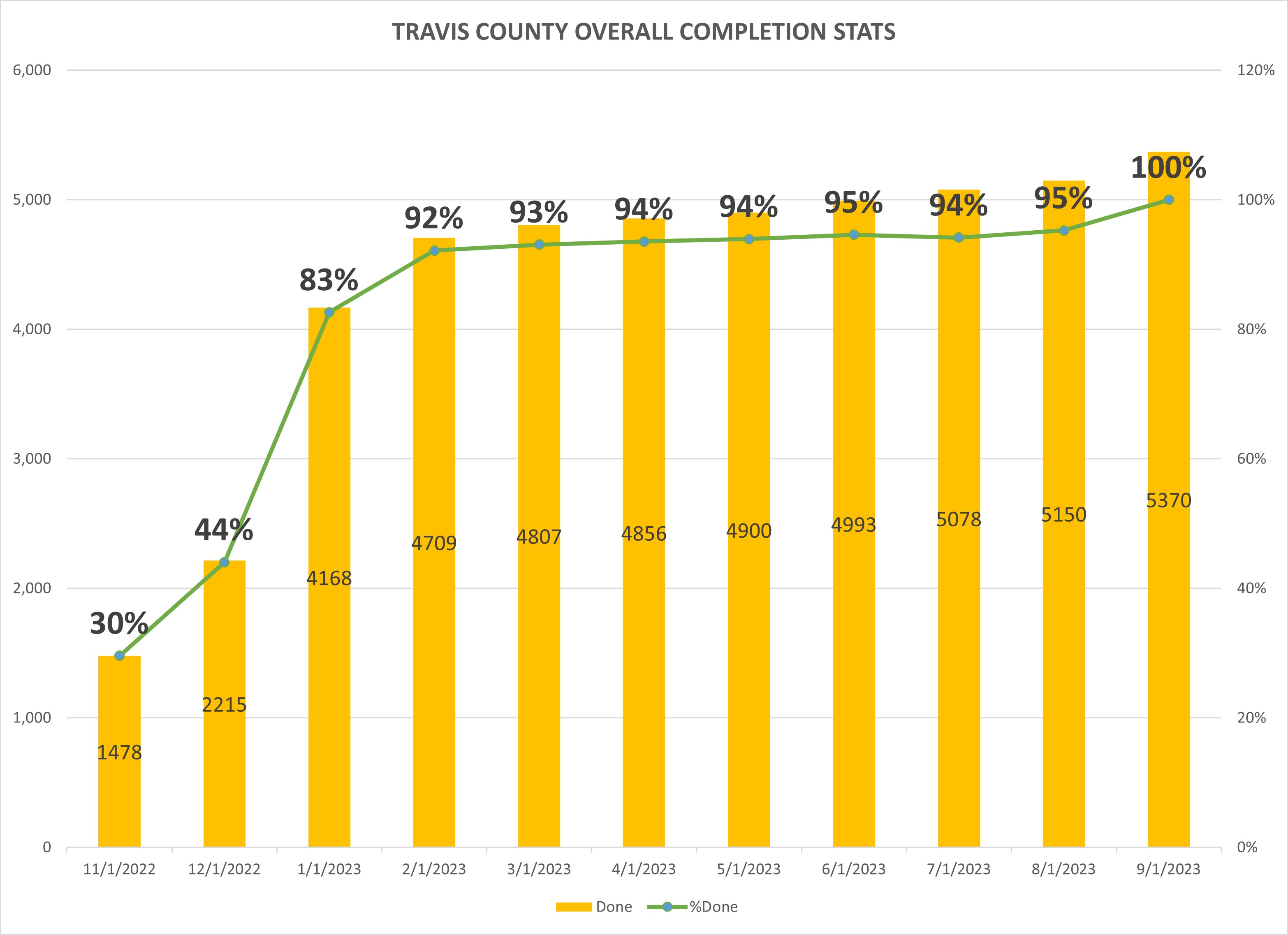
Travis County Annual Cybersecurity Awareness Training (TCACAT)
2024 SCORECARD
2023 SCORECARD
FEDERAL AND STATE REGULATIONS
Health Information Portability and Accountability Act of 1996 (HIPAA)
The HIPAA Act requires the protection and confidential handling of protected health information.
- Health Insurance Portability and Accountability Act (HIPAA)
- HIPAA Privacy Rule
- HIPAA Security Rule
- HIPAA Breach Notification Rule
- HITECH Act Enforcement Interim Final Rule
The State of Texas has expanded requirements for the protection of personal identifiable health information beyond HIPAA.
Justice and Public Safety Information Protection
The FBI and the Texas Department of Public Safety requirements regarding the protection of CJIS systems and information assets.
- Criminal Justice Information Services (CJIS) Documents
- Criminal Justice Information Services (CJIS) Security Policy
Payment Card Industry (PCI)
Contacts
- Travis County HIPAA Compliance and Privacy Officer
- Travis County HIPAA Security Officer
INFORMATION SECURITY CONTROLS
Information Security provides the following guidance aligned with NIST Special Publication 800-53, Revision 5: Security & Privacy Controls for Information Systems & Organizations. (NIST SP 800-53 Rev.5).
| Control Code | Control Name | PolicyTech (New CMS) |
|---|---|---|
| AC | Access Control | 282 |
| AU | Audit and Accountability Control | 280 |
| AT | Awareness and Training Control | 283 |
| CM | Configuration and Management Control | 284 |
| CP | Contingency Planning Control | 278 |
| IA | Identification and Authentication Control | 285 |
| IR | Incident Response Control | 277 |
| MA | Maintenance Control | 287 |
| MP | Media Protection Control | 288 |
| PS | Personnel Security Control | |
| PE | Physical and Environmental Protection Control | 290 |
| RA | Risk Assessment Control | 291 |
| CA | Security Assessment and Authorization Control | 292 |
| PL | Security Planning Control | 293 |
| SR | Supply Chain Risk Management Control | 294 |
| SC | Systems and Communications Protection Control | 295 |
| SI | System and Information Integrity Control | 296 |
| SA | System and Services Acquisition Control | 297 |
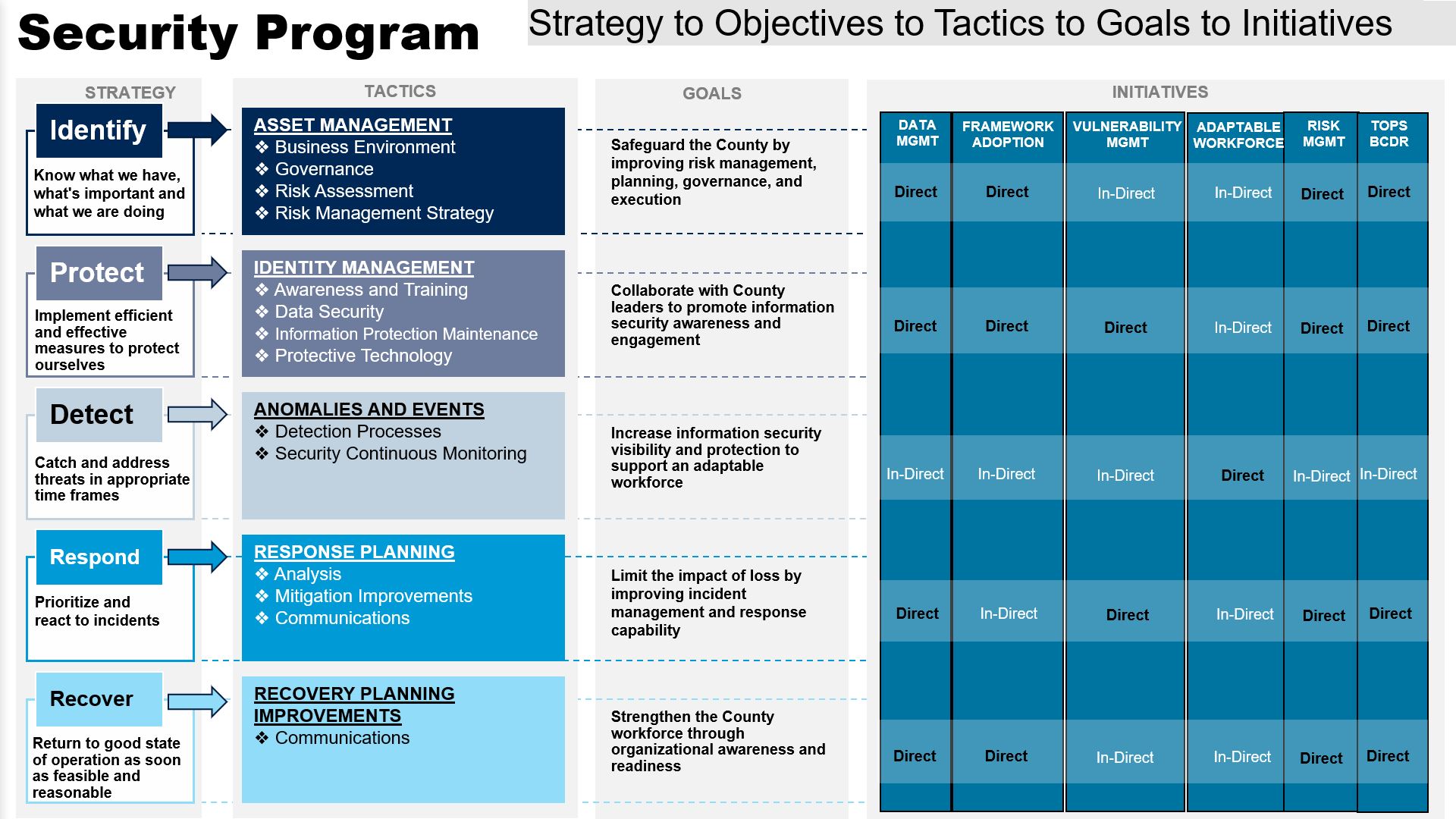
SECURITY PROGRAM
The Information Security Program directly and in-directly achieves the framework guidelines following set goals and initiatives.
Read more about the Information Security Program and your Accountability and Responsibility here at the County.